Opinion
Latest about Opinion

I wanted Nintendo to wow me with the Switch 2 – instead it’s made me hug my ROG Ally X handheld even closer
By Matt Hanson published
Opinion Underwhelming graphics and stupidly high game prices mean the Nintendo Switch 2 is dead to me already.
I didn’t care about Copilot, but this massive upgrade could make Microsoft’s AI the personal assistant I’ve always wanted
By John-Anthony Disotto published
Microsoft just announced some major upgrades to Copilot, and I think it might be the AI companion I've been waiting for.

The rise of APIs
By Lara Fox published
With the rise of AI, APIs are crucial for integrating AI into apps, chatbots, as well as automating workflows.

How the rise of machine identities is reshaping cybersecurity
By Spencer Young published
AI-driven identity security is redefining cybersecurity -protecting machine identities and mitigating evolving digital threats.

Digital Transformation starts with data transformation
By Marty Andolino published
Successful digital transformation requires leadership that champions a data-driven culture.
Striking the right balance – AI’s role in HR transformation
By TechRadar Pro published
Balancing AI’s efficiency with human trust: how HR leaders can navigate responsible AI adoption.
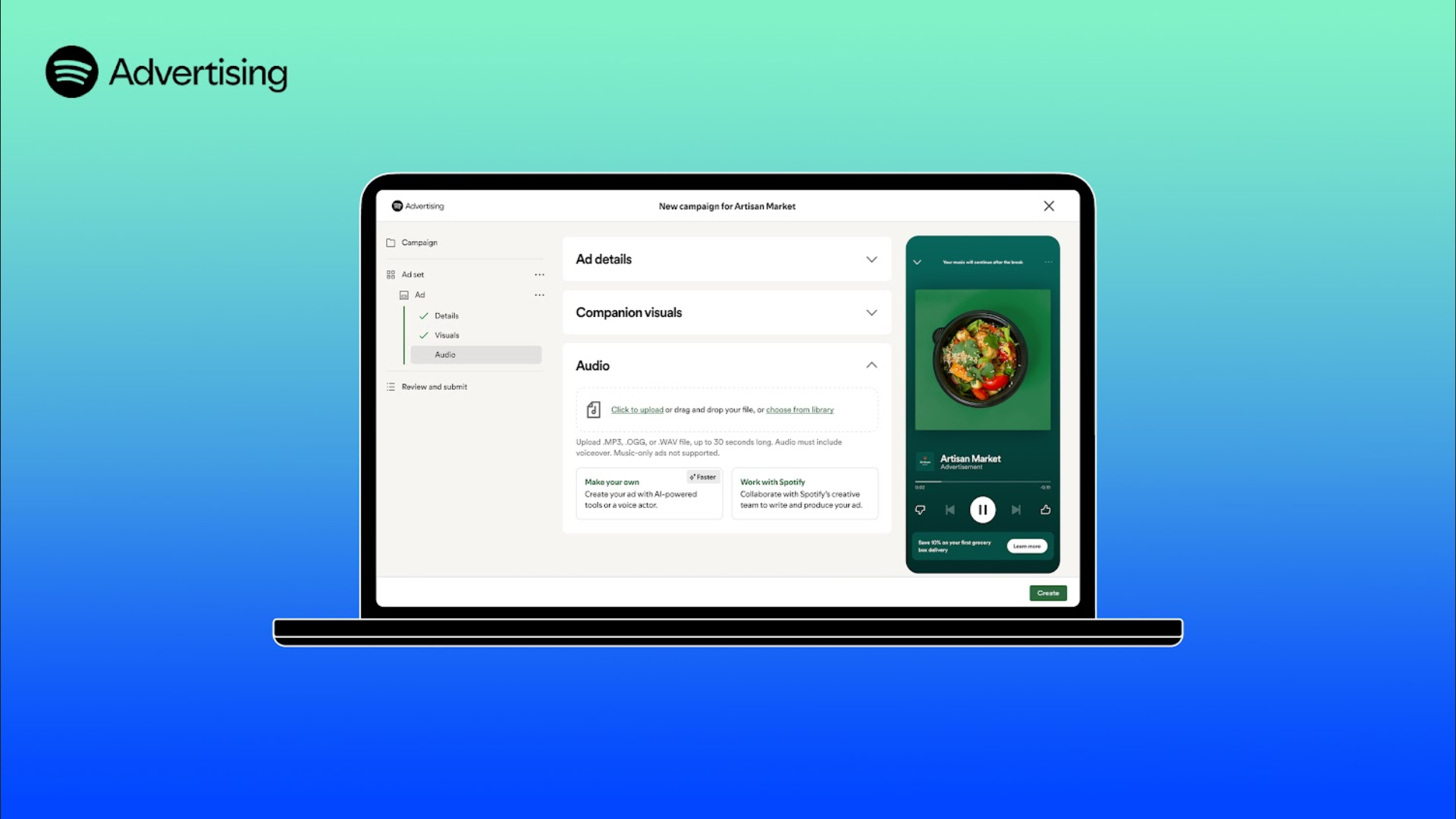
Spotify is about to be flooded with AI-made ads, and I wonder if it will make much of a difference to businesses
By Eric Hal Schwartz published
Spotify’s new AI-powered ad tool may not be the solution they claim.

5 reasons VPNs are obsolete and what businesses should use instead
By Martin Cannard published
Find out why businesses need to abandon VPNs and what should take their place
Get daily insight, inspiration and deals in your inbox
Sign up for breaking news, reviews, opinion, top tech deals, and more.

