Malware
Latest about Malware
Thousands of websites have now been hijacked by this devious, and growing, malicious scheme
By Sead Fadilpašić published
Scheme grew from 35,000 websites to 150,000 websites in just a matter of weeks.

Adapting the UK’s cyber ecosystem
By Ricardo Ferreira published
How the UK can strengthen its cybersecurity landscape, and why the nation’s ongoing commitment to its digital defenses is more crucial than ever.

Dangerous new CoffeeLoader malware executes on your GPU to get past security tools
By Sead Fadilpašić published
A new loader was spotted sporting some creative solutions to remain hidden.

Malicious npm packages use devious backdoors to target users
By Sead Fadilpašić published
Two malicious downloaders were recently found on npm targeting blockchain developers.

Winning the war on ransomware with multi-layer security
By Camellia Chan published
To protect businesses, the economy, and critical infrastructure, cybersecurity must radically rethink its approach.
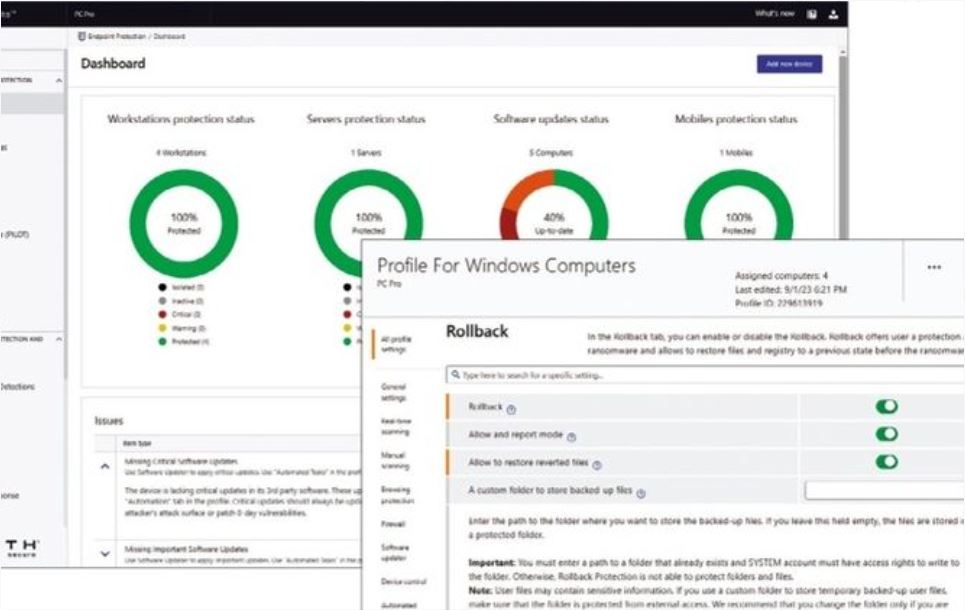
WithSecure Elements EPP and EDR review
By Dave Mitchell published
Not yet ratedAn affordable cloud-managed solution with smart automated remediation services.

Devious new Android malware uses a Microsoft tool to avoid being spotted
By Sead Fadilpašić published
McAfee found at least two apps being used to steal sensitive data.

Why OT security needs exposure management to break the cycle of endless patching
By Andrew Lintell published
Traditional vulnerability management is preventing organizations from staying ahead of the curve and misses the real threats.
Get daily insight, inspiration and deals in your inbox
Sign up for breaking news, reviews, opinion, top tech deals, and more.