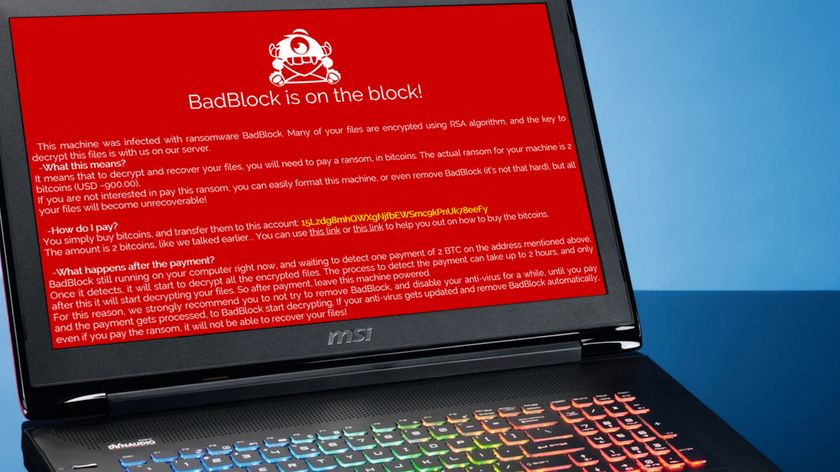
Microsoft Exchange servers are being hacked to deploy ransomware
Multiple threat actors are on the hunt for vulnerable Microsoft Exchange servers

Every ransomware attack starts with a compromised endpoint, and to that end, threat actors have now started looking into Microsoft Exchange servers. As per a report published by the Microsoft 365 Defender Threat Intelligence Team, at least one unpatched and vulnerable server was targeted by crooks, and abused to gain access to the target network.
After gaining a foothold, the threat actors lurked around, mapping out the network, stealing credentials, and pulling out data to be later used in a double extortion attack.
After these steps were successfully completed, the threat actor deployed the BlackCat ransomware via PsExec.
Share your thoughts on Cybersecurity and get a free copy of the Hacker's Manual 2022. Help us find how businesses are preparing for the post-Covid world and the implications of these activities on their cybersecurity plans. Enter your email at the end of this survey to get the bookazine, worth $10.99/£10.99.
Potential attackers
"While the common entry vectors for these threat actors include remote desktop applications and compromised credentials, we also saw a threat actor leverage Exchange server vulnerabilities to gain target network access," the Microsoft 365 Defender Threat Intelligence Team said.
While these things are fact, there are a couple of others, currently in the domain of speculation, namely - the vulnerabilities abused and the threat actors involved. BleepingComputer believes the Exchange server vulnerability in question was covered in the March 2021 security advisory, that suggests mitigation measures for ProxyLogon attacks.
As for the potential threat actors, two names are at the top of the list: FIN12, and DEV-0504. While the former is a financially motivated group, known for deploying malware and ransomware strains in the past, the latter is an affiliate group usually deploying Stealbit to steal data.
"We've observed that this group added BlackCat to their list of distributed payloads beginning March 2022," Microsoft said about FIN12. "Their switch to BlackCat from their last used payload (Hive) is suspected to be due to the public discourse around the latter's decryption methodologies."
Are you a pro? Subscribe to our newsletter
Sign up to the TechRadar Pro newsletter to get all the top news, opinion, features and guidance your business needs to succeed!
To defend against ransomware, Microsoft suggests businesses should keep their endpoints updated, and monitor their networks for suspicious traffic. Deploying a strong cybersecurity solution is always a welcome idea, too.
Via: BleepingComputer
Sead is a seasoned freelance journalist based in Sarajevo, Bosnia and Herzegovina. He writes about IT (cloud, IoT, 5G, VPN) and cybersecurity (ransomware, data breaches, laws and regulations). In his career, spanning more than a decade, he’s written for numerous media outlets, including Al Jazeera Balkans. He’s also held several modules on content writing for Represent Communications.