What is a VPN? VPN meaning explained in 2025
VPNs have never been more popular – but what are they, exactly?

- What is a VPN?
- The best VPNs
- How VPNs work
- VPN benefits
- What devices can I install a VPN on?
- The cost of a VPN
- How to pick a VPN
- The different types of VPN
- Are VPNs legal?
- Can you trust a VPN?
- Do VPNs slow your device down?
- Free VPN apps
- Are free VPNs safe?
- How to avoid dodgy VPN apps
- VPN jargon buster
VPNs (or virtual private networks) are popular security tools. In a few clicks, a VPN will boost your digital privacy, prevent snooping, and even help you unblock streaming content from around the world. Still, you might wonder what they are, exactly – and you wouldn't be alone.
Today's best VPNs are massively commercial and user-friendly. They're also must-have tools for anyone who cares about their online privacy or getting around pesky bans, geo-restrictions, and censorship.
So, keep reading, and I'll walk you through everything you need to know about VPNs – minus the jargon. I've also included a glossary at the end of the article that contains all of the most common terms we throw around when talking about VPNs.
What is a VPN?
Technically, a VPN is any tool that redirects your internet traffic through an additional location and encrypts the data in the process. The good news is that there are tonnes of commercial VPN apps out there - and you don't need to be a tech expert to use them.
VPNs shouldn't be confused with proxies. They do the same thing, sure, but without the encryption that makes VPNs such valuable (and secure) tools.
A VPN grants you improved online security, privacy, and anonymity, as well as access to previously geo-restricted content. Think shows, movies, news outlets, and even social media sites.
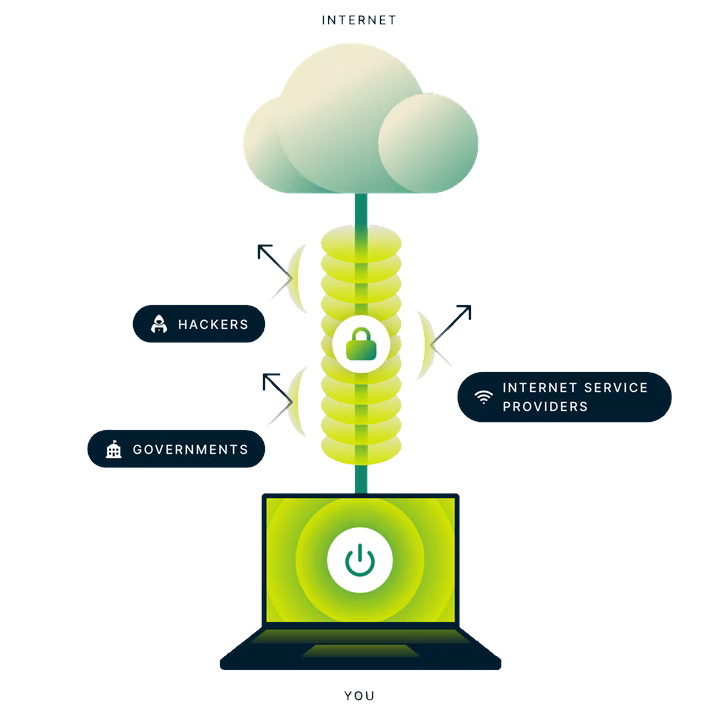
When a reliable VPN encrypts your data, it prevents any third-party snooper from keeping tabs on your online activity. Routing your traffic through a remote server replaces your IP address (your device's unique digital signature), and fools the sites you visit into thinking you're somewhere else.
Get daily insight, inspiration and deals in your inbox
Sign up for breaking news, reviews, opinion, top tech deals, and more.
For example, if I connect to a VPN server in New York, sites and services will read the new IP address and think I'm physically in the States. As a result, I'll see content local to the area and country.
When you connect to a VPN, websites, apps, and services see requests coming from the VPN server, rather than your device, making it almost impossible for cybercriminals, websites, advertisers, and even governments to track what you're doing.
The best VPNs today
Looking for the cream of the crop? Here are today's top three VPNs.
1. The best VPN in 2025: NordVPN
NordVPN is hands-down the best VPN right now. With built-in ad blocking and virus protection, you get all the protection you could want for half the price of ExpressVPN. If that's not enough, NordVPN is one of the fastest services on the market and has an unbeaten track record when it comes to unblocking streaming content.
See for yourself, risk-free, with a 30-day money-back guarantee.
↪ Read more in my NordVPN review.
2. The best cheap VPN: Surfshark
If you want sheer value for money, Surfshark never disappoints. It's a budget-friendly VPN that packs a ton of features into its plans—and it's more than capable of accessing your favorite streaming platforms, too. With unlimited devices, you can protect every device you own without breaking the bank.
Get a third month of coverage for free by taking advantage of Surfshark's 30-day money-back guarantee.
↪ Read more in my Surfshark review
3. The best VPN for beginners: ExpressVPN
Using a VPN for the first time might seem like a daunting prospect—luckily, ExpressVPN does all the hard work for you. Its automation and one-click connection mean you don't have to spend time tweaking the settings. While it's a notably more expensive option, it's well worth it if you just want something you can set and forget.
Compare it to NordVPN with a 30-day money-back guarantee and you'll grab a second month of VPN coverage at no extra cost.
↪ Read more in my ExpressVPN review.
Recent updates
After six years in the top spot, ExpressVPN has dropped in rankings, with NordVPN claiming the throne. With its wealth of features and customizable pricing options, Express couldn't keep up with Nord's value for money. If you want to find out more, check out my recommendations for the best VPN services, or take a look at the results from my latest VPN testing.
How do VPNs work
A VPN works by keeping your real information hidden—protecting your identity, and spoofing your location to let you access apps, sites, torrents, and content anywhere in the world, with total peace of mind.
Whenever you go online, your device—whether that be a computer, laptop, smartphone, game console, or anything else—is constantly sending out data requests and receiving information back. Your browser might send a request to Twitter or Facebook for a particular account, for instance, and then receive the latest page.
Some of this data can be seen by your internet service provider (ISP), and if you're using a public Wi-Fi hotspot, or even Wi-Fi that isn't your own, it can be intercepted by the hotspot operator or any nearby hacker.
The website you're visiting may also be able to find out much more about you, including your approximate location, browsing activities, device information, and even your personal data.
VPNs use encryption protocols to secure your data. These protocols are specific instructions designed to make your data unreadable to anyone who doesn't have the decryption key—usually your device and the website you're trying to access. There are plenty of protocols out there, and some providers even create their own (such as ExpressVPN with Lightway, and NordVPN with NordLynx), but the most common ones are:
The combination of encryption and routing your traffic through a VPN server creates a tunnel for your data, hiding your real data from snooping third parties. Those same websites that would otherwise see all of your information, now see the information of the VPN server, and are none the wiser.
The servers are usually owned by the VPN providers, too, but it's not uncommon for some of the lower-ranking providers to rent servers. Renting servers usually means slower speeds, less bandwidth control, and sometimes even potential security risks. So it's important you pick the right service rather than picking one at random.
That hacker sitting in the corner of the coffee shop setting up a "free Wi-Fi" hotspot won't be able to see your information as they comb through the traffic. Instead, they'll just see a scramble of letters, numbers, and symbols that make no sense whatsoever, and would take an eternity for them to crack.
VPN benefits
There are lots of good reasons to invest in a VPN—from boosting your online privacy to bypassing pesky blocks and bans. Here are the biggest and best benefits of using a VPN.
Online security: connect to a VPN on your computer, phone, or tablet when using public Wi-Fi and its encryption hides everything you're doing online, immediately protecting you from hackers, rogue hotspot operators, and others who might want to steal your personal information.
Bypass web censorship: sometimes, a network prevents access to specific sites—your school might block YouTube, for instance. Connect to a VPN, and the network can't see the sites you're visiting anymore. That means it can't block them, either, and you'll be able to browse the web as usual.
Similarly, visit a country where content is censored, and you might find social networks, international sites and other areas of the web are unavailable. But again, connecting to a VPN means the censorship systems can't see or block the sites you're visiting, and you can access whatever content you wish.
Get around geo-blocking: streaming sites often restrict content to viewers in particular countries, a strategy known as geo-blocking. If a show is only on US Netflix, for example, you won't be able to view it in the UK. Connect to your VPN's New York server, though, and Netflix may think you've relocated, and allow you to stream whatever US-specific content you need (although you should note that some providers work better than other VPNs for Netflix).
The same goes for live-streaming. If there is a sporting event happening on TV in your home country, but you happen to be abroad on holiday, it's 99% likely that the broadcaster will geo-block that coverage. Using a VPN, you can change your location so your laptop, tablet, phone, or TV streaming device thinks it is back in your country. That should let you watch as normal.
Travel: using a VPN to get to a new virtual country can bring financial benefits. Flights, hotel rooms, and all kinds of web services may be priced very differently around the world, and appearing to be in a different country could get you a much better deal.
Anonymity: simply connecting to a VPN immediately makes you more anonymous online, helps to conceal your identity from websites and advertisers, and reduces the chance of anyone tracing a particular internet activity back to you.
What can't a VPN do?
Complete anonymity: even the best VPN services can't protect you completely in every situation. If you log into an online account, then that site knows exactly who you are—whether you're using a VPN or not. Websites use cookies and other tricks to recognize you and log information about your activities. VPNs help, but they don't guarantee total online anonymity.
On top of that, while a VPN service provides safety in numbers, it is in no way a guarantee of total anonymity. If a provider is served a warrant and gag order by authorities, they may be forced to log your activity without telling you. This is a very rare occurrence, and some providers have even gone to court to prove their claims. Like PIA, who proved its no-logs policy not once, but twice.
Avoiding malware: there are an increasing number of VPNs with virus protection and vice versa—see our list of the best internet security suites—virtual private networks can't themselves deter or erase viruses, malware, or online scams. For that, you'll still need a suitable antivirus program (even a free antivirus is better than nothing).
Getting free TV streams: you may see many providers talking about how they're a great VPN for streaming and, as described above, that's true enough when it comes to watching overseas shows and sports. But a VPN won't suddenly give you a free account for Netflix, Disney Plus, Amazon Prime Video, or any other paid-for streaming service.
What devices can a VPN run on?
Custom apps: it's typically straightforward to use a VPN on desktops, laptops, mobiles, and tablets, even if you're a total beginner. Most VPN providers have software for Windows, Mac, Android, and iOS, and getting started can be as easy as installing the appropriate app for your device.
Some providers have support for other platforms. They might have apps for routers, Amazon Fire TV, Android TV, Chrome OS, Linux, and more. That's handy if you're unblocking US Netflix or other content, as you're able to stream it directly on your smart TV.
Manual setup: the best VPNs have detailed guides on setting up their services on other devices. Take ExpressVPN, for example. It doesn't just have a powerful range of mobile and desktop apps, it also has setup guides for Apple TV, Chromebook, Nvidia Shield, PlayStation, Roku, Xbox, LG, and Samsung Smart TVs, and more.

How many devices can I protect with a VPN?
Most providers allow you to set up the VPN on as many devices as you like, but there is one potential catch: they'll often restrict the number of devices that can be connected at the same time. This limit can be as low as five, so if your family is sitting around the smart TV, two using the VPN on mobiles, and two on apps, all while you're streaming US Netflix, you won't be able to connect another device until you disconnect one of the others.
If this might be a problem, look out for VPNs that give you extra support. Many now support ten simultaneous connections, and some have no fixed limits at all (like Surfshark). Most providers clearly display their limit on the website, but they might describe it in one of two ways: "we support up to five devices", or "we support up to five simultaneous connections." That wording is key, because some providers offer an active install limit, rather than a simultaneous device usage limit.
How much does a VPN cost?
Average pricing: premium VPNs range anywhere from around $2 to $12 a month, largely depending on the length of the subscription. Free VPN trials are available from most providers (often in the form of a money-back guarantee) if you'd just like to see how the technology works.
One thing to be aware of is that although VPN providers mostly always show their pricing in terms of monthly cost, they will still charge you the full price upfront when you sign up.
VPN plan lengths: commercial VPN companies typically offer monthly and annually billed plans, with some offering subscriptions of up to five years. In most cases, the longer the subscription, the better value you'll see.
Monthly plans are typically priced at $10 to $13. Pay for a year up-front, and this usually drops to around $4 to $8. Sign up for a long-term plan and there are even more savings to be found. The likes of PureVPN and Ivacy have been known to charge less than $2 a month for plans of three to five years, and occasionally, we've seen other providers ask for less than a dollar a month.
These ultra-low headline prices might catch your eye, but think carefully before you sign up. A good VPN needs numerous fast servers, knowledgeable developers to write top-quality apps and keep them updated, and expert support staff available 24/7 to help you solve any technical issues. That's expensive, and if a VPN isn't charging enough money to cover everything it should be doing, that's inevitably going to compromise the quality of the service.
Here's an up-to-date list of the best VPN deals currently being offered by today's top providers:
Free VPNs: some VPNs are entirely free and unrestricted. These have a lot of appeal but beware: free VPN apps have previously been used to install malware, log your browsing history, inject ads into web pages, and more. Even if the provider is entirely honest, providing fast and reliable service with regularly updated apps and helpful support is expensive. No free VPN can compete with the top paid providers.
How to choose a VPN
There are several factors to consider when you're choosing a VPN, and their importance will depend on what you'll be using yours for—so think about what you want to do with it before you buy.
A VPN with a large server network is a good sign, but check whether they have them in the locations you care about. If you're planning to use your VPN on a multitude of laptops, mobiles, streaming devices, and routers at once, then make sure that there are enough simultaneous connections to cover them all.
If you want to use your VPN for streaming, then check that it unblocks your favorite streaming service, while keen torrenters will want a VPN with plenty of P2P servers and a working kill switch.
Of course, there's the price to consider—more expensive doesn't always mean better, and there are some great value options available on this list. And you can always give the best VPNs a whirl with a free trial, too.
The different types of VPN
It's tempting to think of VPNs as a homogenous group of products. However, as with most things in life, a closer look reveals that there are all sorts of VPNs out there. A day-to-day user will typically come across these three types:
Personal VPN
As the name suggests, a personal VPN is designed for everyday users, normal people, and not corporations and businesses. These are the VPNs you see popping up in YouTube sponsorships and ads. With a personal VPN, you'll connect to a VPN server, your traffic will be encrypted, and you'll be able to go about your regular browsing with boosted digital privacy.
Remote access VPN
Remote access VPNs help workers connect to a network (and all of the apps and data living on it), securely, which is especially important for folks working from home or outside the office. To use a remote access VPN, you'll need to authenticate your credentials and install the client software onto your device.
Site-to-site VPN
Similar to remote access VPNs, site-to-site VPNs help workers in massive businesses connect to one another's networks. So, if you have several offices working side-by-side, it'll let you share resources, files, and data safely (thanks to its encryption).
Are VPNs legal?
VPNs are legal to use in most countries worldwide, but there are some exceptions: Iraq, North Korea, and Turkmenistan all ban VPNs entirely. China allows you to sign up for a VPN, but only if it's a government-approved provider. The UAE, Oman, and several other countries have regulations that may make some VPN use illegal. Russia and Turkey haven't outright banned VPNs, but they may block access to some VPN servers and provider websites.
This isn't an exhaustive list, and the rules may change at any time as countries introduce new regulations. The key point to remember is it's your responsibility to understand the rules, so do some research before you travel.
Although VPNs are entirely legal in North and South America, Western Europe, Oceania, and most of the rest of the world, there are a couple of points to keep in mind.
First, VPNs are often used to fool streaming platforms into thinking you're in another country, for example allowing you to access US-only Netflix content from anywhere in the world. That's not illegal, but the streaming companies don't like it, and some say they might close your account if they catch you doing this.
Note: it's very unlikely to happen, but be careful—don't complain to Netflix's customer support if a VPN doesn't work.
The second is that even where VPNs are legal, they're still often used for illegal activities. If you share copyrighted material, hack a network, or sell on the dark web, then you can still get into trouble if you're caught. If in doubt, check the VPN provider's terms and conditions page—there's almost always a list of activities it doesn't allow.
Remember: for the most part, it's not the VPN that's illegal, it's what you're doing with it that might be.

Are VPN services trustworthy?
We believe the top VPNs are trustworthy, and doing their very best to protect you and your privacy.
Secure technology: you can see this in the comprehensive technologies they'll develop to keep users safe. ExpressVPN's TrustedServer scheme uses multiple layers of protection to ensure every server is running using the same software, for instance, making it far more difficult for an attacker to compromise.
Even if we imagine a movie-type scenario where a hacker breaks into the ExpressVPN offices and tries to insert a secret back door into the server code, that still wouldn't be enough. The system won't accept changes until a developer has gone through authentication to prove their identity, and the code has been reviewed by someone else.
VPN audits: many providers are increasingly demonstrating their privacy credentials by putting themselves through third-party VPN audits. Typically, these allow experts from respected names like PricewaterhouseCoopers, Leviathan, and Cure53 to inspect a provider's apps, check their servers, look at source code, run in-depth technical tests, and generally confirm they're protecting your data in the ways they claim. Check out our guide on what a VPN audit involves to find out more.
Audits are helpful because they're not just about catching fraudulent VPNs that might log your browsing: they can also confirm the apps and servers are working properly and don't have any bugs or other deficiencies which might leave you exposed.
These steps can't guarantee a VPN is safe, but they're a very positive indicator. And although it's important to look for a trustworthy VPN, it's worth keeping the issue in perspective. Password managers, web hosts, cloud backup companies, and many other services also have huge responsibilities when it comes to looking after your data, but most make little effort to prove they're doing this properly. The best VPNs do considerably more to reassure potential customers and show how they're protected.
Do VPNs affect performance?
Connect to a VPN and the service must encrypt and decrypt your traffic, then route it through the VPN server. The extra overhead is likely to reduce your internet speeds meaning yes, VPN services can affect internet speed. Distance matters, so the effect will be even more noticeable if you're using a server on the other side of the world.
But in reality, you're unlikely to see any significant difference when using a good premium VPN. We fully test VPN performance in our reviews, and the top providers deliver very high speeds just about everywhere. You should have no trouble with browsing, streaming, or any of your regular web tasks.
There's a possible exception with online gaming, where it's vital to have the best possible speeds. But you can turn off the gaming VPN temporarily to restore your normal performance.
Alternatively, some VPNs have a feature called "split tunneling," which allows you to specify apps that bypass the VPN and use your regular connection, instead. Set this up, and you could have most of your traffic protected by the VPN, but allow your games or other performance-sensitive apps to connect as normal for the maximum possible speed.
What free VPNs are available?
Some commercial VPNs have limited free plans. PrivadoVPN, Proton VPN, Atlas VPN, Hide.me, Windscribe, and others all allow you to sign up and use a basic version of the service at no cost, for as long as you like.
These free versions often have significant restrictions. Most limit your data use to around 1GB to 10 GB per month (although ProtonVPN's free plan supports unlimited usage.) You often won't get access to all a VPN's locations; some free VPNs don't allow you to choose a location at all, they select the nearest for you. And they may omit significant features, such as the ability to unblock streaming sites.
These limited free plans could be enough for simple tasks, though. Even if you can't live with the restrictions for long, they're a convenient and risk-free way to try out a VPN app, and see how its apps work for you. They're also far more trustworthy than most of the anonymous free competition because you can clearly see who runs them, how they're funded, read detailed privacy policies, and generally understand more about how they work.
The dangers of free VPNs
Search for "VPN" on Google Play, and you'll find apps from more than 200 providers, with many being entirely free. It's easy to wonder why you'd ever use anything else, but our testing and experience show these smaller VPNs usually aren't worth the gamble.
Many seem untrustworthy, for instance. They don't tell you who runs them. They may not have a website. Some are only contactable via a generic Gmail address. They don't tell potential users anything about the encryption or other technologies they use. In some cases, we've even noticed providers who steal the privacy policy from a legitimate VPN and pretend it's their own. Basically, there are very few truly free VPNs.
Even if a free VPN is honest, use the service, and you're likely to pay in other ways. Constant ads, for instance, every time you do anything on the app. And with all the surrounding waiting, you might have to do it because you're connecting to an overloaded server with far too many users.
Yes, true, they're free, but is it really worth trusting your internet activities to a dubious-looking provider, just to save the $2 to $4 a month you might pay for some legitimate and high-quality commercial servers? We say not—especially with the quality on offer from the best cheap VPNs.
If you have zero budget and there's no other option, free VPNs might just about work for unblocking Netflix or other streaming sites. But don't leave them connected (or, ideally, even installed) when you're using the web for anything else, and don't ever use them to protect anything privacy-critical.
How to avoid dodgy VPNs
You're using a VPN because you don't trust your websites and ISP with your data, and that makes sense. But are you sure you can trust your VPN? Are you positive it's not logging your online activities, and selling them off to the highest bidder?
VPN providers know this is a big concern, and most claim that they don't keep logs of the websites you visit, the files you download, or any other details of what you're doing online.
These are reassuring words, but can you really trust them? If a provider is logging and selling your browsing history, it's unlikely to admit this on the website.
To be really safe, it's best to pick a VPN that has put its services through a VPN audit as described above. Many of the best providers are already doing this, calling in independent experts, allowing them to inspect their systems, and verifying that they're living up to their privacy promises.
VPN terminology glossary
- AES encryption: a secure form of encryption that defines how to encrypt and decrypt your data. First established in 2001 by the U.S. National Institute of Standards and Technology (NIST), AES now represents the global standard of encryption.
From messaging apps like WhatsApp and Signal to privacy software like VPN services, it is now employed for a vast array of technologies. You might have come across different denominations like AES-128, AES-192 and AES-256. The number at the end relates to the length of the cipher’s key. As a rule of thumb, more bits make for stronger encryption.
Click to read more ↓
- Browser history: the list of all the web pages you access with your browser, together with some other metadata like the page title and time you visit the site. Even though your web browsing history is generally locally stored, cookies and other web trackers associated with the pages you visit may collect some of your personal information. The good news is that secure browsers offer a private browsing or incognito mode for extra privacy. This means that both your browsing history and data associated with the session are never recorded.
- Dynamic multi-point VPN: a routing technique generally used by organizations to create a VPN with multiple sites. It differs from a static VPN as the data moves from one site to another without the need to pass through its central server. A DMVPN gives businesses more flexibility to tailor networks according to their needs and make wide communication easier, while cutting operational costs. This form of dynamic tunneling is supported on Cisco IOS-based routers, Huawei AR G3 routers, and on Unix-like operating systems.
- Domain Name System (DNS): think of DNS as the internet's phone book. Every time you look for a certain site on the web—like techradar.com, for example. You do so by typing the domain name associated with it. At the same time, browsers list websites according to their IP addresses—a unique number linked to each device existing on the net. DNS is the technology that enables your machine to match domain names with their respective IP so that the internet can load the resources you are looking for.
- DNS leak: using a VPN means that, theoretically, all of your DNS requests are protected by the encryption tunnel. However, your security software might fail to properly protect you. When a DNS leak occurs, your data—like browsing activity and your device IP—may be exposed to attackers. Luckily, there are plenty of free DNS leak testing websites around that you can use to check whether your security software is doing its job.
- Encryption: the process of scrambling your data to make it unreadable for a third party. This means that if attackers manage to access your data, they won't be able to decrypt the information. Different encryption algorithms are responsible for defining the formula through which your data is encrypted and transformed in ciphertext, and then decrypted via a cryptographic key.
Similar to a physical key, the data can be accessed with the right key only. There are different types of encryption. Symmetric encryption, like AES used in VPNs, is a straightforward process where everyone uses the same secret key. Asymmetric encryption uses a public key to scramble the data and a private key for decryption. - Gateway: the networking device that links different remote sites, devices, and networks together within a VPN infrastructure over a non-secure network like the internet. It can connect multiple VPNs, too. Generally, a physical router or a VPN gateway can also be a server, firewall, or similar. It allows the routing and blocking of VPN traffic, providing services like IP address assignment and management.
- Geo-restrictions: policies and technology (usually firewalls) that restrict access to content according to a user's geographical location. Internet geolocalization tactics include monitoring your IP address, or GPS in case of a mobile connection.
Also known as geo-blocking, it is largely used by international streaming services for copyright and licensing reasons. Other web services might apply geo-restrictions to enforce censorship, location-based pricing, as well as fraud prevention and online gambling according to local laws. - Internet Protocol Security (IPsec): a secure group of protocols that provides secure encrypted communication between different devices. Often used to build up a VPN tunnel infrastructure, IPsec works by authenticating, encrypting, and decrypting packets of data. It can be operated in a transport mode, like in end-to-end communications, for example, to protect specific data content, and in a tunnel mode to encrypt the entire IP packet.
- IP address: if DNS is like the phone-book of the internet, IP addresses are the phone numbers filling the list. A series of numbers that define the type and geographical location of each device existing in a network: from web pages to your laptop, smartphone, home router, or printer. Computers use IPs to exchange communications between each other, while defining where everything is on the internet or inside a specific network.
- Internet service provider (ISP): a company that provides both individuals and businesses with an internet connection. ISPs might deliver other services, too. These include browser packages, emails, domain registration, and web hosting. They can also differ in the type of connection supported, such as cable, fiber, or DSL, as well as according to their broadband speed. Examples of ISPs include AT&T, Comcast, BT, Virgin, and Renater.
- Kill switch: a feature that stops your data from leaking to the web. It works by continuously monitoring your connection to fix accidental data exposure. If your VPN connection drops, the kill switch will automatically disconnect your device from the internet until a secure VPN protection is restored. Although not all providers offer a kill switch, they are becoming a standard among the most private VPN services. These generally activate the option by default to ensure extra users’ privacy.
- Layer 2 tunneling protocol (L2TP): an encryption protocol used to support VPN connections. While IPsec is used for functionality purposes like encrypting and decrypting information, L2TP creates a secure space where these encrypted data packets can safely move between networks.
These two components are always used together, under the denomination of L2TP/IPsec, as without encryption the tunneling will be worthless. Please note that L2TP/IPsec are no longer secure encryption protocols. - No-logs/zero-logs VPN: a security policy offered by the most private VPN services, it guarantees that the provider doesn't store any sensitive users’ data. While some information, like email addresses and payment preferences, might be recorded for functionality reasons, data that could reveal your identity and online activity is never logged. An increasing number of VPN providers are now undergoing regular independent audits of their security policies to support their no-logging claims.
- Remote access VPN: a type of VPN that allows users working remotely to establish secure and encrypted connections between their colleagues, devices, and apps used within their network. For a remote access service to work, every device needs to have the VPN client app installed. With remote work getting increasingly popular across different sectors, remote access VPNs can boost businesses’ data security while cutting operations expenses.
- Secure socket layer (SSL): a security protocol responsible for encrypting HTTP traffic. This means all the ongoing connections between users’ devices and web servers. It works by establishing a secure authentication process between two devices known as a handshake. SSL ensures a high degree of data privacy and data integrity for every exchange of communications. First developed in 1995, SSL technology has now been replaced by Transport Layer Security (TLS). However, this is still referred to as SSL.
- Simultaneous connections: the number of devices that you can use at the same time with one VPN subscription. However, if you install a VPN on your router, all the devices connected to it will be protected by the VPN connection despite counting for one device.
- Smart DNS: a proxy server that masks your real location by rerouting your DNS in an entirely different country. Similar to a VPN, SmartDNS allows you to bypass geo-restrictions applied to content. However, instead of simply hiding your IP address, it actually replaces the DNS so that it cannot reveal your real geographical position.
The downside is that your devices and data won't be protected by any form of encryption. This is why many good streaming VPNs nowadays also offer SmartDNS technology to boost their unlocking capabilities while keeping their users’ privacy secured from snoopers. - Port forwarding: a more straightforward method of moving data inside a defined network, it provides a bridge between devices located on an external network (WAN)—like the internet—with those on a private local area network (LAN). VPN port forwarding is generally used for multiplayer gaming, P2P torrenting activities, web hosting, and remote desktop access. As port forwarding can create security issues, many VPNs don't support the practice, and users are advised to experiment with caution.
- Proxy server: the middleman between your device and the internet. Similarly to a VPN, a proxy replaces your IP address with the one linked to its server. You can use a proxy server to bypass geo-restrictions, anonymize your activities, boost your online security, and save bandwidth data. Despite acting like a VPN, proxy servers don’t encrypt your data in transit. What’s more, many proxies are free to use, meaning they might share users’ information with third-party advertisers.
- VPN connection: a secure and encrypted connection between your device and the internet provided by VPN software. An active VPN connection creates a VPN tunnel to protect users’ data in transit, preventing snoopers from accessing your information. It also spoofs your real IP location so that every time you connect to one of its available servers, your device will look like it is based in your chosen location.
- VPN client: an application that allows a user to control a VPN connection. The VPN client is the end point within a VPN infrastructure and initiates the connection with a chosen server. It first grants access to a specific IP address, then redirects the data in transit through the VPN tunnel.
- VPN protocol: a set of instructions that VPN apps and servers use to establish a secure connection and communicate with each other. A VPN protocol defines every aspect of your VPN connection: from the way the app logs into the server and thus authenticates its identity, to the encryption used to secure your data. VPNs generally offer several protocols that users can choose from.
- VPN provider: the company that provides a VPN service to individuals and/or organizations. Different providers might be owned by the same parent company, although they typically operate independently.
This is something that you might want to check if you want to make sure who is actually handling your data. For example, ExpressVPN, Private Internet Access (PIA), and CyberGhost VPN are all part of the wider Kape Technologies group. - VPN server: think of a VPN server as a powerful computer designed to host and deliver the encrypted tunnel responsible to protect your data. Every time you access a website, the server decrypts your traffic to send it to the intended destination. The VPN server is also the one defining the IP address that your ISP will see when you connect to a VPN. It then encrypts any information before reaching back to your device. VPN servers can be both virtual and physical. However, the latter are more popular as they are considered to be safer.
- WireGuard: the newest VPN protocol on the market. Originally developed for Linux-based operating systems, WireGuard is now widely employed by many VPN services as it offers several advantages. These include a simpler coding infrastructure, making it easier to fix bugs and vulnerabilities.
WireGuard is also faster and more secure, as it uses modern cryptography code that allows more reliable connections. It also has some downsides, like using the same key by default. This means that if a hacker manages to get into the server and steal your key, they may also be able to decrypt your traffic—but almost all implementations of WireGuard remedy this with the addition of some code.

River has been writing about VPNs since 2020, and helps take care of cybersecurity content on TechRadar—ranging from breaking news pieces, reviews, and buying guides.
Disclaimer
We test and review VPN services in the context of legal recreational uses. For example: 1. Accessing a service from another country (subject to the terms and conditions of that service). 2. Protecting your online security and strengthening your online privacy when abroad. We do not support or condone the illegal or malicious use of VPN services. Consuming pirated content that is paid-for is neither endorsed nor approved by Future Publishing.

Mike is a lead security reviewer at Future, where he stress-tests VPNs, antivirus and more to find out which services are sure to keep you safe, and which are best avoided. Mike began his career as a lead software developer in the engineering world, where his creations were used by big-name companies from Rolls Royce to British Nuclear Fuels and British Aerospace. The early PC viruses caught Mike's attention, and he developed an interest in analyzing malware, and learning the low-level technical details of how Windows and network security work under the hood.
- Chiara CastroNews Editor (Tech Software)
You must confirm your public display name before commenting
Please logout and then login again, you will then be prompted to enter your display name.


